GitHub - shauryasharma-05/PortableKanBan-Hash-Killer: PortableKanBan stores credentials in an encrypted format.

Accused killer pit two in fight before choking, torturing WL woman found near Kentland, court doc says

Killer immunoglobulin-like receptors and HLA act both independently and synergistically to modify HIV disease progression | Genes & Immunity

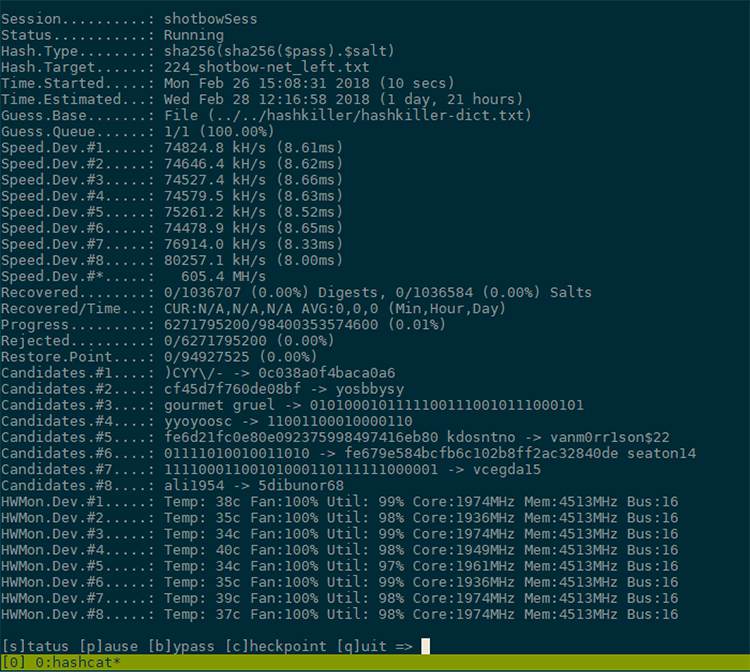
BleepingComputer on Twitter: "Once a threat actor gains access to the NTLM hash, it's as simple as running it through Hashcat to dehash the password. Now the threat actor has both the